Hackers rely on a variety of tools to force access to your online accounts. Here is a selection of the best in the field.
Password theft and trafficking is – as we know – one of the pillars of cybercriminal activity. According to security researchers from Digital Shadows, more than 24 billion username-password pairs have been stolen in the past six years before ending up in hacker forums and other illegal stores.
But how do hackers manage to recover all these passwords? What techniques do they use? According to the Digital Shadows report, phishing by e-mail obviously remains the royal way to access the secret codes of Internet users. But there are also more specialized and lesser-known tools that hackers use to achieve their ends.
Redline, the data vacuum cleaner
Because phishing may not always work or be suitable, hackers can use malicious code to siphon passwords stored on a system. One of the most used software in this case is Redline Information Stealer. It costs around $200 and deploys fairly easily. Hackers often send it through booby-trapped messages, in the form of an Excel extension (XLL).
Once installed on a computer, it will search it from top to bottom. It will particularly scrape data stored in web browsers, where it can recover cookies or, precisely, passwords. Redline is also able to detect the existence of certain processes, such as antivirus ones. This makes it possible to create relatively complex attack strategies. If it works, it’s the jackpot. Because compared to phishing, the malware makes it possible to recover many identifiers at once.
OpenBullet, the credential stuffing specialist
The pirate who holds a batch of identifiers will try to make the most of this asset. How ? By applying these identifiers on other sites. Everyone knows, in fact, that many Internet users use the same password on several sites. Of course, there is no question of doing this by hand. According to Digital Shadows, the most popular software for automating this task is OpenBullet. It is often used in conjunction with a proxy service, so that the IP address can be changed with each connection attempt. This allows hackers to remain discreet, and to prevent an online service from blocking them.
Available for free on GitHub, Open Bullet was originally created by security researchers to make penetration testing easier. For it to work well, the user must nevertheless define “configs” that allow the software to properly manage the authentication process. Concretely, the tool must know where to put the username and password and be able to detect a successful connection. But don’t panic: these configs are sold in hacker forums. Pirates therefore really do not have to break their heads.
HashCat, the fingerprint breaker
When hackers manage to access user databases, they generally do not recover plaintext passwords, but only their cryptographic fingerprints (“hashes”). This is a one-way mathematical transformation that allows validating a password entry without having to manipulate the actual password. In theory, no online service should store plaintext passwords, only cryptographic fingerprints.
By definition, there is no simple method to find a password from its hash. The only way to do this is to calculate the hashes of many passwords and compare them with that of the password you are looking for. It is often long and tedious, which is why hackers use software, in this case HashCat.
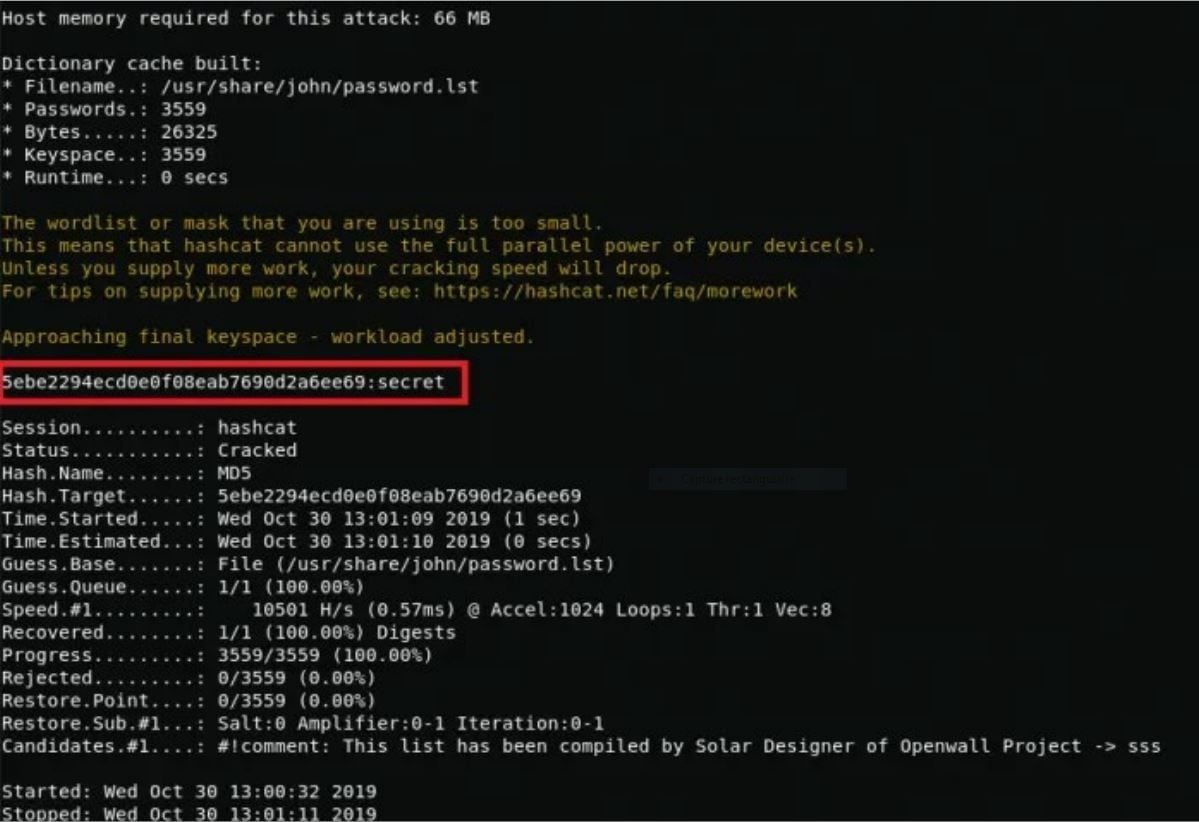
Its advantage is that it allows you to define calculation strategies to go faster. One can, for example, load one or more “dictionaries”, ie large compilations of frequently used passwords. Hackers can also define “masks” for these dictionaries, in other words patterns for constructing passwords. Example: a word that begins with a capital letter and ends with a number and a special character. This is one of the most used patterns by Internet users. But it is possible to program much more complex patterns. The goal is to avoid as much as possible calculation by brute force, stupid, nasty and very slow.
Digital Shadows
[related_posts_by_tax taxonomies=”post_tag”]
The post Here are the software hackers use to steal your passwords appeared first on Gamingsym.
