Security researchers at HP Wolf Security managed to isolate a malware campaign that used OpenDocument text files for distribution. This particular campaign was part of a larger one that was targeting the hotel industry in several South American countries that included Brazil, Argentina, Chile, Peru, Columbia and Costa Rica.
What makes this particular malware campaign interesting is the use of OpenDocument text files in the attack. All major office applications, including Microsoft Office, LibreOffice and Apache OpenOffice, support the format, which makes it an ideal format to carry out attacks.
Since it is less commonly used in malware attacks, it is a file format that computer users may be less suspicious about. Emails with Office document attachments, PDF documents or even executable files are commonly used and users may be more aware of the potential danger of these documents.
The threat actors referenced remotely hosted objects in the document but did not include any macros; this was done to evade detection, as antivirus engines may flag documents that make use of macros.
The researchers discovered the malware campaign in late June and noticed that the malicious OpenDocument documents were not picked up by any of VirusTotal’s antivirus engines in the first week of July.
Fake Booking Request emails
The attackers used fake booking requests in emails to get the attention of hotel employees. The malicious OpenDocument files were attached to the emails and designed to look like legitimate requests. In one email, the document’s title suggested that it was a booking request.
The document opened in the Office program that was set as the default file handler for the Office format when the user clicked on it. When the document was loaded, an error message was displayed that prompted the user for action. It displayed a cryptic message — This document contains fields that may refer to other files. Do you want to update the fields in this document? — with yes and no options.
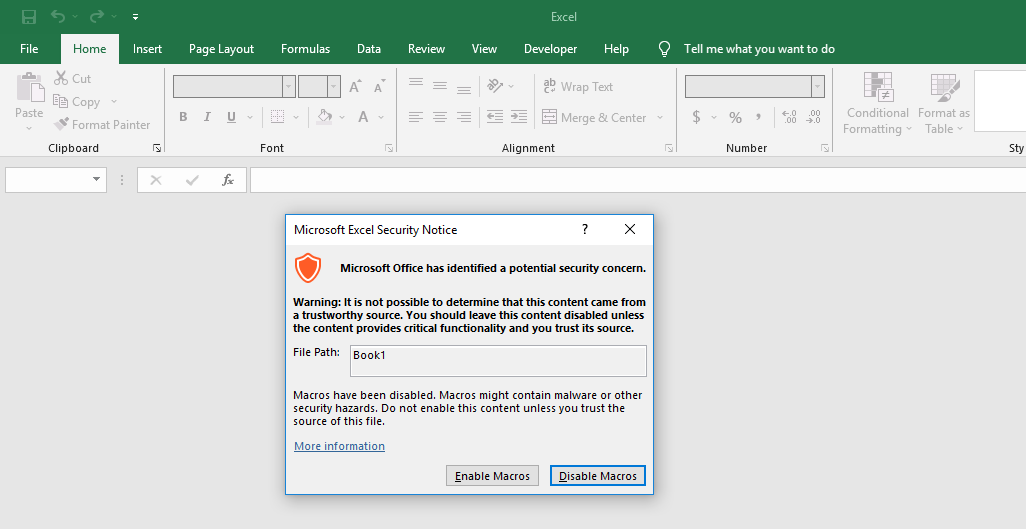
Selecting “yes” opened an Excel spreadsheet on the system. The Excel spreadsheet included a macro. Most Office programs prevent the execution of macros by default, but give users options to enable the macro.
Another prompt was then shown in the spreadsheet application, for instance Microsoft Excel, that prompted the user to enable macros. The selection of “enable macros” triggered the infection chain, which led to the infection of the computer with the AsyncRAT payload.
Microsoft plans to block macros in Office documents that come from the Internet by default in the future and remove the “enable” prompt for these documents. While users may still enable macros for specific documents, doing so requires more work and should prevent accidental execution of documents with macros for the majority of users in the future.
The infection chain
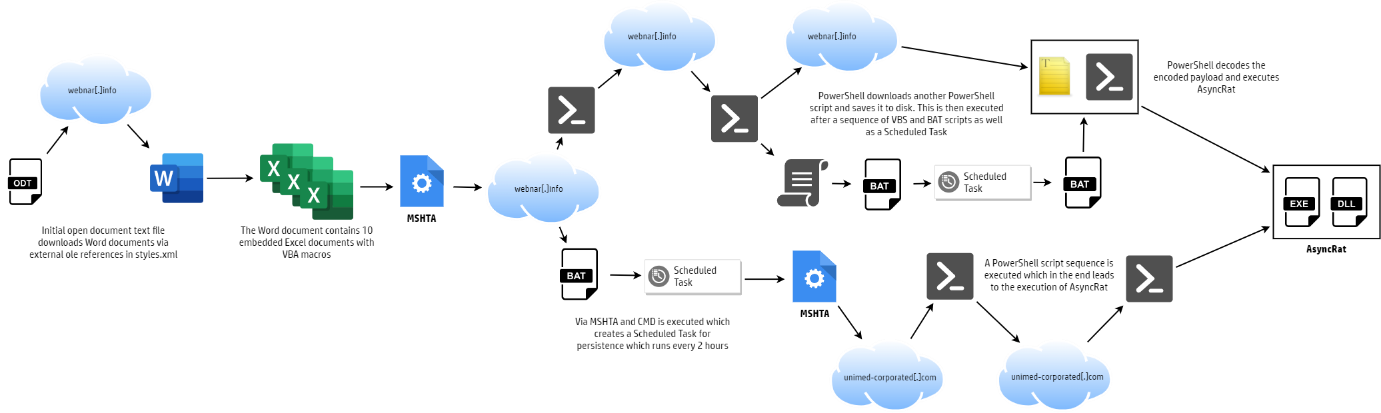
OpenDocument files are not used often in malware campaigns. The document that was used in the campaign did not include any macros, hidden or not, when it was analyzed. HP security researchers discovered that the document was referencing Object Linking and Embedding (OLE) objects that were hosted remotely. One of the analyzed documents referenced 20 remotely hosted objects.
The referenced objects were downloaded from the referenced remote location when the user selected the “yes” option after opening the documented that was attached to the email. Downloads included Excel spreadsheets, which included macros. The user was then prompted by the Office application to enable macros or keep them disabled.
The macro that is part of the Excel documents uses the mshta.exe tool of Windows to download and execute code from the Internet. Things start to accelerate from there as a “complex chain of PowerShell, VBScript and batch scripts” was executed. In the end, the open source remote access trojan AsyncRAT was decoded and executed.
The malware creates a scheduled task in an attempt to make the infection persistent. The task is designed to launch the malware in two hour intervals.
Conclusion
Attackers are always hunting for stealthy ways of delivering malware that evades endpoint security. This campaign illustrates how OpenDocument text files can be abused to deliver malware through external OLE references with extremely low detection rates.
Like most malware campaigns, this campaign requires that victims become active. The victim has to open the included file attachment and respond to two different prompts before the actual malware is downloaded and executed on the system. Canceling or denying any of the prompts would stop the attack before it really begins.
It comes as a surprise that emails from outside the organization that contain documents with attachments are still a viable attack vector after all these years.
The use of OpenDocument file formats serves several purposes. Employees may be trained to look out for certain file formats in email attachments, but likely not .odt files or other OpenDocument files. The file itself contains no macros, which antivirus engines may notice and block automatically or warn users about.
The fact that no antivirus engine detected the OpenDocument file used in the campaign as malicious for over a week confirms that the evasive method worked. HP security researchers found a second campaign in July that used a Microsoft Word document instead of an OpenDocument file as the email attachment. Nearly half of all antivirus engines on VirusTotal flagged the Microsoft Word document.
Organizations may improve their defenses in several ways. Besides training employees and raising awareness, which only goes that far, it is new defensive options that could be implemented to reduce the risk of infection. The execution of attachments in virtual environments could be a viable option, as it prevents the infection of the underlying system if the executed document is malicious.
Home users may use virtual machines or sandboxing to launch file attachments and suspicious files without running the risk of infecting the underlying operating system. A program like the free Sandboxie Plus may be used to execute files in a sandboxed environment. Use of virtual machines requires additional steps, such as launching the virtual machine when it is needed, but provide similar protections.
Now You: do you open file attachments in emails?
Thank you for being a Ghacks reader. The post OpenDocument text files (.odt) malware campaign discovered appeared first on gHacks Technology News.
