A modern smartphone stores a lot of confidential and valuable information. No one wants their phone to fall into the hands of someone else. That is why users install protection in the form of passwords or pattern keys on their devices.
BY TOPIC: How to set Apple Watch faces to change automatically based on time and location.
After all, often the information in the phone is more expensive than the phone itself. And we are not talking about moral inconvenience due to data loss. A smartphone is our key to bank accounts, payment systems, online stores. I don’t even want to imagine what an attacker can do on your behalf. And if someone other than you knows the password for your phone, then all responsibility for such credulity lies solely with the owner. But the iPhone allows you to know that someone picked it up and took some action with it.
First, you need to understand that in principle, giving access to your iPhone is not a good idea, even if it is your spouse or children. And here the question is not even that a person close to you can find something on the phone that he is not intended to know.
You must understand that the access code is a tool not only for unlocking the phone, but also for the subsequent performance of quite important actions. This includes confirmation of payments in the App Store and iTunes, online and offline purchases in Apple Pay.
BY TOPIC: How to turn on the flash (flashlight) for calls and notifications on iPhone.
How can Screen Time help?
If such a situation has already developed, and other people can use your iPhone by adding their fingerprints or faces to the phone database, then the owner can at least check when his phone fell into the hands of other people. Let’s make a reservation right away that it makes no sense to study the list of applications running in the background. For starters, few people remember which programs were open the last time they used their smartphone. And the person who took your iPhone in his hands could well just close all the software in use, clearing the memory.
This is where Screen Time comes in handy. It will track the unauthorized activity of other users. Of course, this function must first be activated so that it will later record everything that happens to your iPhone. For this:
1. In the application “Settings» find the item «screen time“.
2. In the window that appears at the top, click on the item “Turn on Screen Time“.
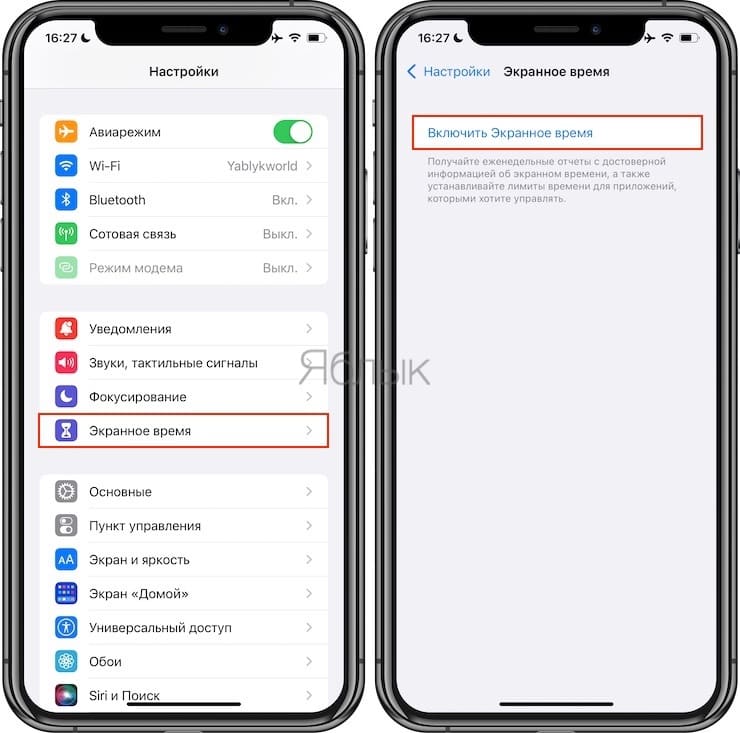
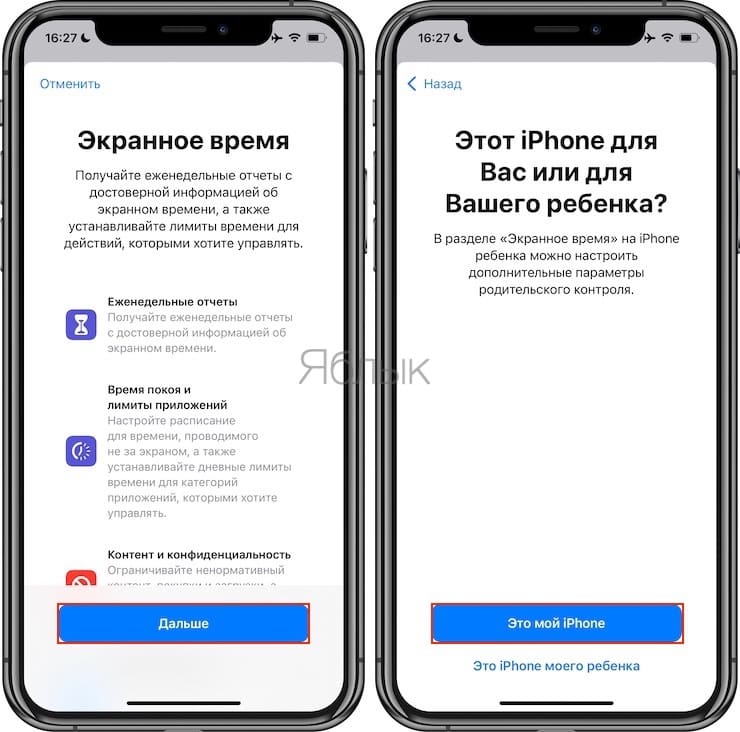
3. On the next screen, click Fartherand then This is my iPhone.
BY TOPIC: How to lower the iPhone screen to reach the top of the display with one finger.
How do you know if someone has used your iPhone?
Again, to find out if someone has used your iPhone, Screen Time must be turned on beforehand. Only in this way it will be possible to distinguish your own activity from outsiders. Here are the required next steps:
1. If you believe that someone has accessed your smartphone, then on the iPhone, go to Settings → Screen Time.
2. In this menu, click on the line “See all activity“. Next, open the “Day” tab, where it will be easier for you to consider extraneous activity.
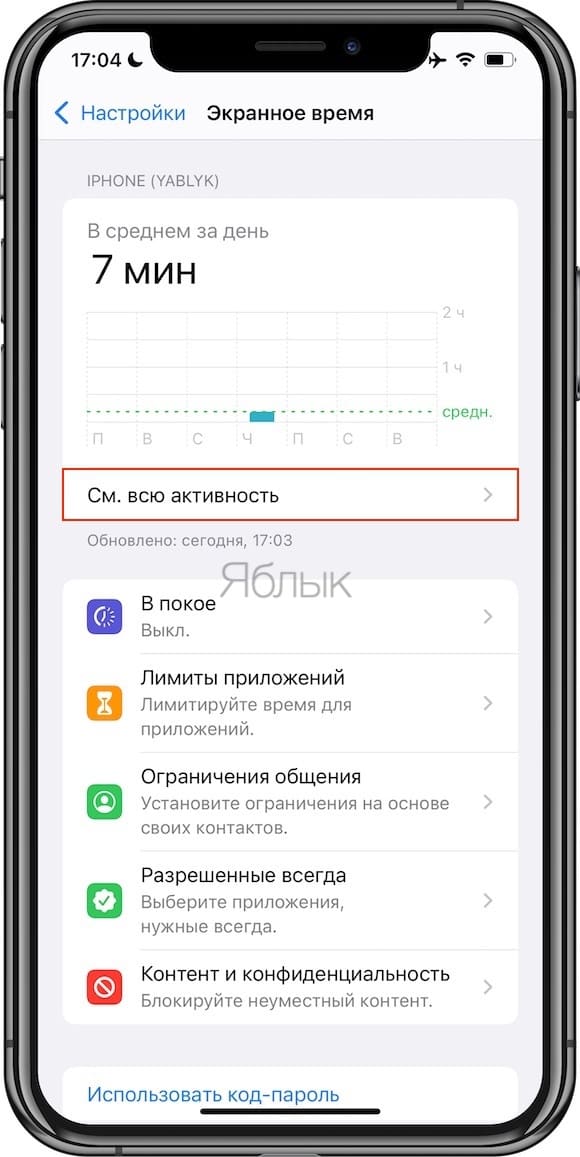
3. A screen will open with a weekly or daily view of iPhone usage. Select the desired day. Below in the section Often used A list of the most used applications will appear.
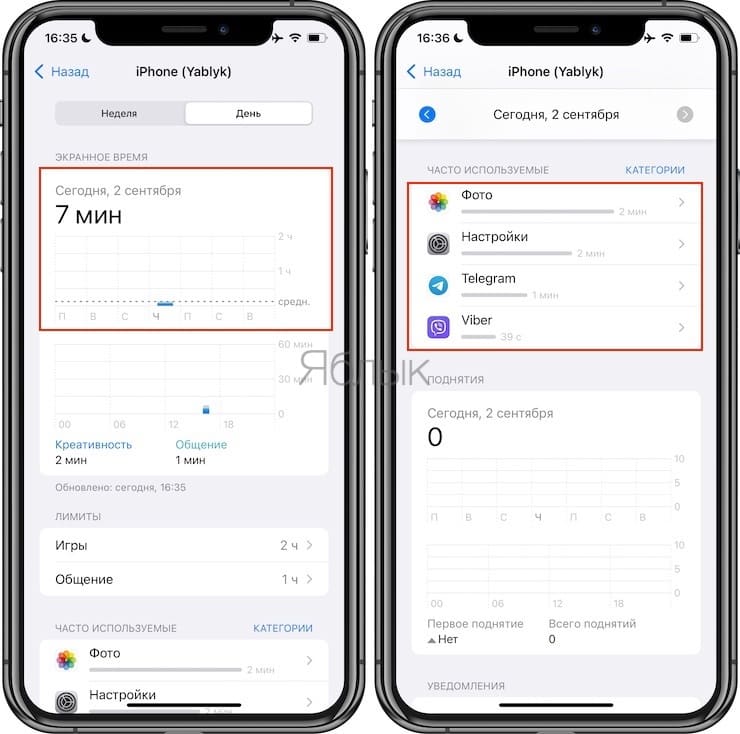
4. By clicking on a certain application, you can get more detailed information about the time of its use. The numbers at the bottom of the grid are tied to the time of day. The scale is evenly divided – 00, 06, 12 and 18 are just the hours in which this or that activity was noted. If you click on the scale, a more specific time value will appear.
It will be most effective to study the breaks between activities. Each such pause means that the user stopped working with his iPhone, putting it down or going to bed. If some activity soon appeared, then someone obviously picked up your smartphone and started working with it.
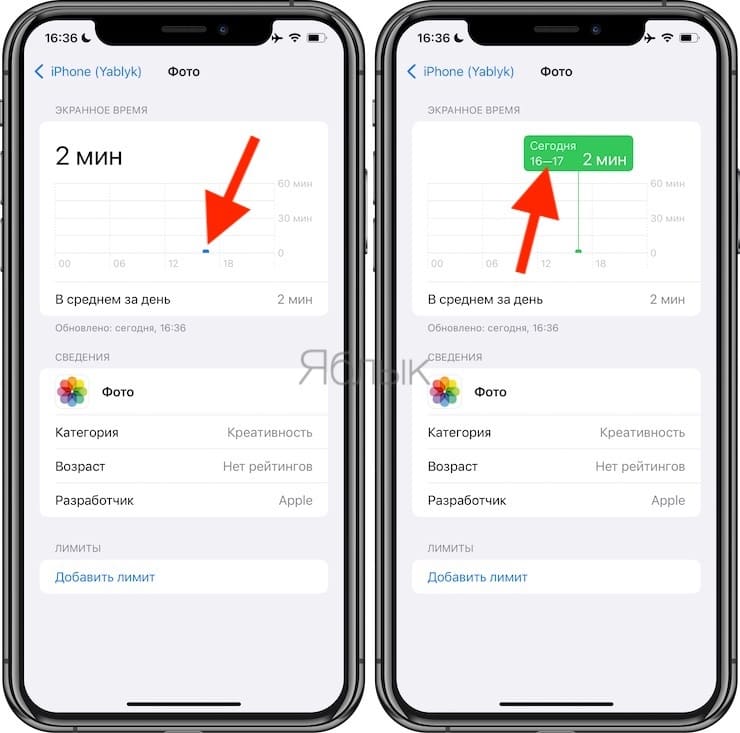
You can also deviate from the time of work. So, you can know for sure that you slept in the period from 23:00 to 7:00 in the morning. If at that time your iPhone was working with certain applications: social networks, instant messengers, then this should make the owner think. Then it’s worth checking another time. If similar matches are found there, then an unauthorized person can be suspected of using your iPhone.
What to do in such a situation is understandable, there are not so many options here. The easiest and most logical thing to do is to ask your partner, friend, or child not to use your iPhone. True, in life such requests are often simply ignored. Then you will have to act more decisively. You can simply set a new access password, making it more difficult than the previous one (you didn’t use the year or date of birth, right?). A more serious step is to remove an alternative fingerprint or face from the database. As a result, no one from the closest circle will be able to access your smartphone.
See also:
.
The post Whether your phone is taken when you sleep: how to find out appeared first on Gamingsym.
