Security researchers have discovered vulnerabilities in Intel and AMD processors that may lead to information disclosure.
Most Intel 10th, 11th and 12th generation processors are affected by a new vulnerability that the researchers have named ÆPIC Leak. The vulnerability is an architectural bug according to the researchers, which sets it apart from Spectre and Meltdown vulnerabilities that have haunted Intel and AMD in the past years.
AMD Zen 2 and 3 processors are affected by a security vulnerability that the researches named SQUID. It is a side channel attack that is targeting CPU schedulers.
The following paragraphs provide a high-level overview of both security issues. We provide links to the research papers and security advisories released by Intel and AMD.
Most home devices with affected processor models should be safe, as the attacks have certain requirements that make attacks on home systems unlikely.
ÆPIC Leak: important resources
Security researchers from Sapienza University or Rome, Graz University of Technology, Amazon Web Services, and CISPA Helmholtz Center for Information Security published the research paper ÆPIC Leak: Architecturally Leaking Uninitialized Data from the Microarchitecture recently.
The name is derived from the Advanced Programmable Interrupt Controller (APIC) and affects all Intel processors that are based on the Sunny Cove architecture. In particular, Ice Lake and Alder Lake processors are affected.
Attackers may exploit the vulnerability to retrieve data from the cache hierarchy. Without going into too many details — the research paper provides all the technical information needed — Æpicleak exploits a bug in Sunny-Cove based processors. When reading data on Sunny-Cove based CPUs, stale data from the superqueue is returned; this is not by design, as it should result in undefined behavior instead according to Intel.
The researchers note that the returned data is not restricted to security domains.
The uninitialized data returned from ÆPIC Leak is not restricted to any security domain, i.e., the origin can be userspace applications, the kernel, and, most importantly, SGX enclaves.
Experiments confirmed that the superqueue is used “as a temporary buffer for APIC requests”. The superqueue contains recent memory loads and stores, and the APIC “only overwrites the architecturally-defined parts of the register and leaves the stale values in the reserved part”.
In other words, attackers may exploit the bug to read data, including AES-NI keys from SGX enclaves.
Several different attack techniques are described in the research paper:
- Leaking data and code pages — The most straightforward attack type combines “Enclave Shaking and Cache Line Freezing” to “leak data (and code) at rest of an SGX enclave.
- Leaking register values — Attack targets a specific cache line to reconstruct the value of the register.
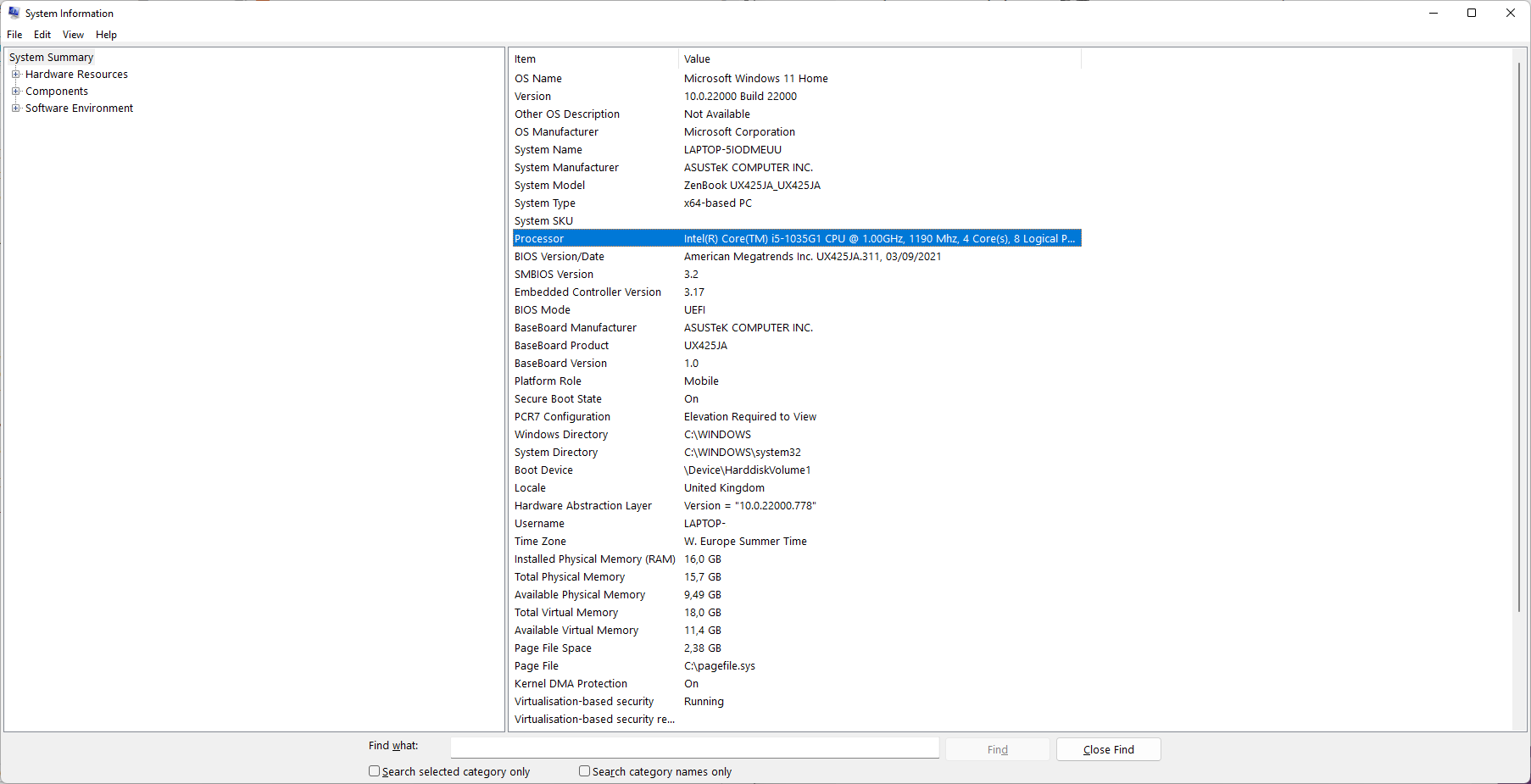
How to look up the processor generation on Windows
Windows users may do the following to check the processor generation of Intel processors:
- Open the Start Menu.
- Type System Information.
- Load the System Information result.
- Check the value of the processor entry, and there specifically the first or the first two digits after the dash, e.g., Intel Core i5-1035G1 is a 10th generation processors.
Sunny-Lake based processors are not vulnerable to Meltdown attacks.
Mitigations and fixes
The vulnerability requires root or administrative level access to the machine to exploit the vulnerability. Most home systems should be safe because of that, but it is still recommended to install updates once they become available.
Æpic Leak requires a hardware fix according to the researchers. They assume that the fix should not be too complex, as older processors are not affected by the issue. The research paper lists several mitigation suggestions, ranging from disabling SGX to disabling caching for EPC.
Intel reveals on the 2022.2 IPU – Intel® Processor Advisory support page that customers should install the latest firmware versions provided by the system manufacturer to address the issue. Intel plans to release SGX SDK updates once the public embargo is lifted.
Intel has released microcode updates for affected processors that are already available on the company’s public GitHub repository.
AMD processors affected by SQUIP vulnerability
A new research paper by researchers from Lamarr Security Research, Graz University of Technology and Georgia Institute of Technology have discovered a new vulnerability affecting certain AMD processors.
Resource links:
- Execution Unit Scheduler Contention Side-Channel Vulnerability on AMD Processors
- SQUIP: Exploiting the Scheduler Queue Contention Side Channel
The linked research paper provides technical details on the vulnerability. Researchers discovered a vulnerability in CPU schedulers of affected AMD processors. SQUIP is the first side-channel attack on scheduler queues, according to the research paper.
The SQUIP attack observes the occupancy level from within the same hardware core and across SMT threads.
An attacker could extract sensitive data from a co-located victim in under 45 minutes, according to tests performed by the research team.
Hardware and software mitigations are suggested in the research paper. One of the easier options is to deactivate SMT or to prevent that processors from different security domains from running co-located on the same core.
The following processors are affected by the vulnerability:
- AMD Ryzen 2000, 3000 and 5000 series
- AMD Ryzen 4000 and 5000 with Radeon graphics series.
- 2nd and 3rd generation AMD Ryzen Threadripper processors.
- AMD Ryzen Threadripper PRO processors.
- AMD Athlon 3000 mobile processors with Radeon graphics.
- AMD Ryzen 2000 mobile processors.
- AMD Ryzen 3000 mobile processors.
- AMD Ryzen 3000, 4000 and 5000 processors with Radeon graphics.
- AMD Athlon 3000 series with Radeon graphics. (Chromebook)
- AMD Athlon mobile processors with Radeon graphics. (Chromebook)
- AMD Ryzen 3000 series processors with mobile graphics. (Chromebook)
- 1st, 2nd and 3rd generation AMD EPYC processors.
AMD users may use System Information to look up the processor. Other options include opening Settings on Windows 10 or 11 devices, and to select System > About to display the processor make and model.
AMD does not plan to release any kernel mitigations or microcode updates for affected processors. Instead, the company offers the following recommendation:
AMD recommends software developers employ existing best practices1,2, including constant-time algorithms and avoiding secret-dependent control flows where appropriate to help mitigate this potential vulnerability.
Thank you for being a Ghacks reader. The post Security vulnerabilities found in Intel and AMD processors appeared first on gHacks Technology News.
